There are the obvious examples: fingerprint scanners that unlock doors and facial recognition that allows payment through a phone. But there are other devices that do more than read an image — they can literally read people’s minds.

In 1963, 250,000 people marched on Washington to demand equal rights. By 1968, laws had changed. But social progress has since stalled.

A new conceptual model depicts the complex relationship between policing and population health.

Most participants in a recent study had no idea that their email addresses and other personal information had been compromised in an average of five data breaches each.

The wearable technology market is booming, with half a billion wearables sold globally in 2020. Apps on these devices, or the devices themselves, often claim to monitor our health to spot illnesses, track our workouts to help us reach our fitness goals, or keep an eye on

The destination of stolen data depends on who is behind a data breach and why they’ve stolen a certain type of data.

The best way to reduce crime in the future is probably what caused it to drop in the first place: helping our families, neighborhoods, and schools raise kids who are respectful of others and don't need to steal to get by

Police academies provide little training in the kinds of skills necessary to meet officers’ growing public service role, according to my research.

Hackers and cybercriminals place a high premium on our mobile phone numbers – with which they can do a lot of damage with very little effort.

If you hear “This call is being recorded for training and quality control,” it isn’t just the customer service representative they’re monitoring.
- By Bill Kovarik

In 1915, Gabrielle Darley killed a New Orleans man who had tricked her into a life of prostitution. She was tried, acquitted of murder and within a few years was living a new life under her married name, Melvin.
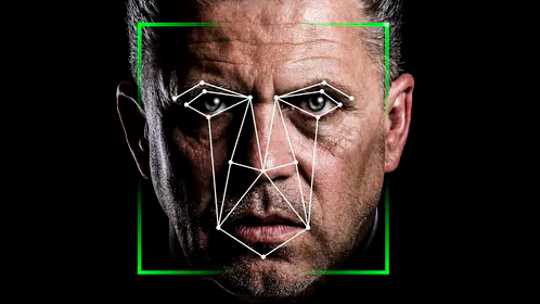
Who owns your face? Of course, a silly question … right? But what about the data generated from your face? And what does it mean to have your face become data?

In recent years, the most popular gadgets sold on Amazon have included a variety of smartphones, wearable tech, tablets, laptops and digital assistants such as Amazon’s Echo Dot. But any device connected to the internet (including almost all of the above) exposes our personal data to a host of threats.

Thomas Hobbes recognized almost four centuries ago, if everyone just does what they please, no one can trust anyone. We end up with chaos, uncertainty and a “war of all against all.”

As the ongoing pandemic has a larger segment of the population working from home — with all of its attendant distractions — and the setting is ripe for exploitation. The humble home router has become the surface attack...
There are those who question the idea of debt forgiveness and call it unfair to those who never took out student debt or already paid it off. As an ethicist who studies the morality of debt, I see merit in the question: Should student debt be canceled?

Since the beginning of the health crisis, courts in many countries have been making a technological shift. The number of proceedings filed online have increased and the same holds for virtual trials.

Facebook has responded to Netflix documentary The Social Dilemma, saying it “buries the substance in sensationalism”.

Drones of all sizes are being used by environmental advocates to monitor deforestation, by conservationists to track poachers, and by journalists and activists to document large protests.

A famous 1990s New Yorker cartoon showed two dogs at a computer and a caption that read “On the Internet, nobody knows you’re a dog.”

Unfairness alone is upsetting – upsetting enough to drive people to punish those who have benefited from unfair outcomes.

The commodification of the internet in the early 1990s brought western societies into the digital age and has changed the way consumers interact with commercial enterprises.
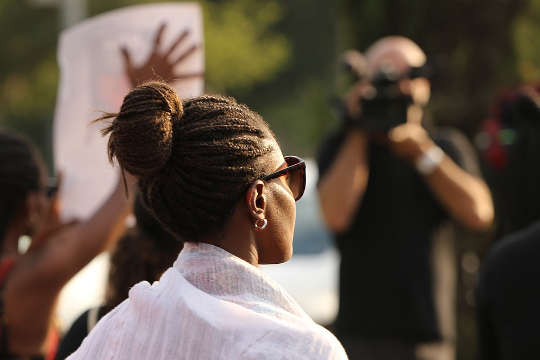
US police forces have been turning to technology to track down Black Lives Matter protestors.